In preview, Silicon Luxembourg gives you all the details of a cyberattack that is currently targeting United Nations employees and many humanitarian organizations all around the world.
by: Delphine Sabattier
photo: Daryan Shamkhali / Unsplash
featured: United Nations headquarters
Listen to article
It is still ongoing! A mobile-centric phishing campaign is targeting non-governmental organizations around the world, such as UNICEF, Red Cross and Red Crescent Societies. The law enforcement and the United Nations have been contacted by Lookout, the mobile security specialist which detected the attack. However, it is not so easy to stop these kinds of malicious campaigns. In an emergency, one of the first things to do is to alert people and that is exactly what we – at Silicon Luxembourg – are doing here.
This phishing attack is quite rare because it is targeted and employs dreadful techniques. As usual in phishing attacks, the goal is to incite to click on a link that leads to a counterfeit site and collects as many identifiers and passwords as possible. But here, the campaign is served through the mail servers specifically used by those working for or with the UN. A JavaScript code logic on the phishing pages can then detect if the page has been loaded on a mobile device. This means, depending on whether the user opens the link in his mailbox from his PC or smartphone, it delivers appropriate content.
“One of the first times we see this happening through a mobile phishing attack.”
And that’s not all. This phishing attack uses a noteworthy functionality that logs keystrokes directly in the password field. Even if the target doesn’t complete the login activity by pressing the login button, or entering a wrong one, the information is still sent back to the malicious actor: “One of the first times we see this happening through a mobile phishing attack”, reports Bastien Bobe, Lookout mobile security expert.
And we are sure this won’t be the last time. “Mobile phishing is an increasingly real risk for enterprises, mainly because employees are using more and more their own devices”, Lookout says. Last but not the least, mobile users are more exposed to these kinds of traps, as mobile web browsers truncate URLs. That makes it harder for the victims to discover a deceptive URL.
This attack has been flushed out thanks to a mobile security tool using artificial intelligence. “Lookout Phishing AI” locates new domains and SSL certificates and analyzes their activity over time. It learns to recognize a fake site and warn users accordingly. From there, the security teams go back to the host. In this case, it is a Chinese host of low reputation, a hosting “bulletproof” named Shinjiru. “It is unlikely that the host collaborates”, explains Bastien Bobe.
As far as Lookout knows, this attack has been live since March 2019. How many victims have succumbed to date? Hard to say. The specialist observed one hundred of login and password attempts on one of the corrupted domains, since last July.
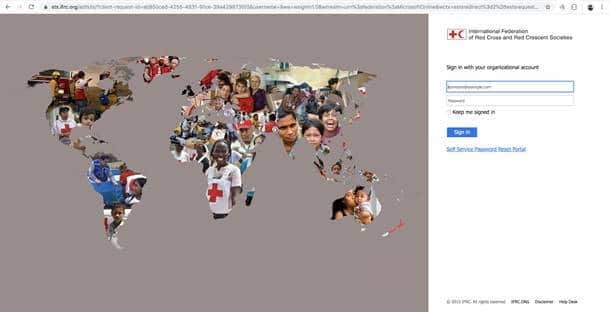
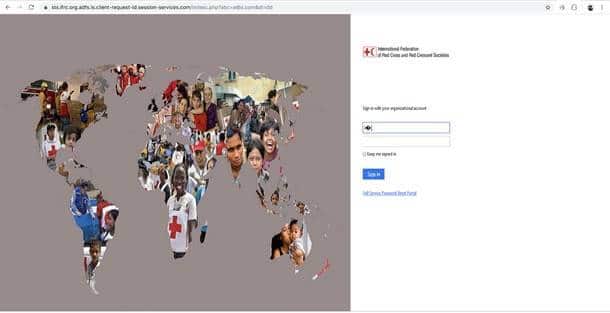
Below is a sample of one of the live phishing sites discovered by Lookout researchers. The legitimate login page, and the phishing site mimicking the Office 365 login page for employees of the International Federation of Red Cross and Red Crescent Societies.